[ad_1]
One in-demand certification for cybersecurity is the CISSP Certification, which is often generally known as Licensed Data Programs Safety Skilled. CISSP is a globally acknowledged certification specializing in numerous features of cybersecurity, together with threat administration and safety insurance policies. It’s provided by (ISC)², i.e., The Worldwide Data System Safety Certification Consortium. These CISSP Interview Questions and Solutions will enable you put together your self for security-related interviews and CISSP examination preparation as properly.
Cybersecurity is a broad and complicated area that includes defending pc methods, networks, and knowledge from unauthorized entry, assaults, and injury. Cybersecurity professionals be sure that data is accessible solely to those that have the correct authorization and put in place measures to forestall unauthorized alteration, modification, or deletion of knowledge. The rising demand for cybersecurity professionals is prone to persist as organizations attempt to strengthen their cyber defenses due to the persistent cyber threats.
Changing into a cybersecurity skilled includes a mix of training, hands-on expertise, and steady studying. CISSP Certification is a vital milestone for cyber professionals because it validates their expertise, opens up profession alternatives, offers trade recognition, and contributes to steady studying and growth.
Now, let’s discover the CISSP Interview Questions and Solutions in in line with the eight domains of CISSP. We’ve greater than 30 CISSP interview questions and solutions line up beneath.
Area 1. Safety and Threat Administration Interview Questions
1. Clarify the CIA triad.
The CIA triad consists of three core ideas: Confidentiality, Integrity, and Availability. These ideas kind the idea for designing and implementing safety measures to guard data belongings.

Confidentiality: Confidentiality signifies that data is barely obtainable to licensed people, entities, or processes. It offers with safeguarding knowledge towards unauthorized entry and disclosure.
Integrity: Integrity ensures that data stays correct, full, and dependable all through its lifecycle. It includes defending knowledge from unauthorized modification, alteration, or corruption.
Availability: Availability ensures that knowledge is accessible when wanted by licensed customers. It includes making certain that methods, networks, and knowledge stay operational and accessible, even within the face of disruptions, failures, or assaults.
2. What are the steps it’s good to take for threat administration in your group?
There are 5 primary steps concerned in threat administration. They’re
Determine Dangers: This step consists of Figuring out potential dangers that might have an effect on the goals of the group. This offers with figuring out inside and exterior elements that will result in threats.
Assess Dangers: Consider the affect of recognized dangers. This step includes analyzing the chance of every threat occurring and estimating the severity of its affect. Threat evaluation methods equivalent to qualitative evaluation and quantitative evaluation may be employed.
Threat Prioritization: It offers with rating dangers in line with their affect to find out which of them require fast consideration for mitigation. Take into account elements such because the group’s threat tolerance and obtainable assets when prioritizing dangers.
Threat Mitigation: This step includes creating and implementing methods to scale back recognized dangers by taking preventive measures to scale back the probability of dangers. Widespread threat mitigation methods embody threat avoidance, threat switch, threat discount, and threat acceptance.
Threat Monitoring: This step offers with repeatedly monitoring the effectiveness of threat administration measures. This step includes monitoring key threat indicators (KRIs) and efficiency metrics to trace the standing of recognized dangers.
3. What’s Privateness? What are the OECD privateness tips?
Privateness is the power of people to manage entry to their private knowledge and to make selections about how that data is collected, used, shared, and saved by others. Private knowledge have to be properly protected to adjust to present privateness legal guidelines and to guard the worth of the data and of the group itself.
The Group for Financial Cooperation and Growth (OECD) is a world group devoted to establishing worldwide requirements and insurance policies, in addition to discovering options to social, financial, and environmental challenges.
OECD tips are primarily based on these following ideas:
- Assortment limitation precept
- Knowledge high quality precept
- Goal specification precept
- Use limitation precept
- Safety safeguards precept
- Openness precept
- Particular person participation precept
- Accountability precept
4. Are you able to counsel some strategies to implement personnel safety insurance policies and procedures in your group?
- Candidate Onboarding: A brand new candidate represents a threat to safety, and each group ought to ensure that firm safety insurance policies, acceptable use insurance policies, and different agreements are reviewed previous to giving a brand new worker their system credentials.
- Candidate Termination: Previous to an worker leaving, person system entry must be disabled, and the details about the worker’s termination must be conveyed to all related events inside the group.
- Job Rotation: Job rotation is an HR administration technique the place staff are moved by way of quite a lot of positions or duties inside a corporation as a substitute of being completely assigned to a single function or division. Job rotation is helpful for shielding towards fraud and offers cross-training in order that a person can’t commit fraud and might cowl it up.
- Implement the Want-to-Know and Least Privilege Precept: This Want-to-Know precept states that people ought to solely be granted entry to data or assets which are needed for the efficiency of their job obligations. The precept of least privilege (PoLP) dictates that people must be granted the minimal stage of permissions required to carry out their job capabilities.
- Insurance policies: Implement personnel safety insurance policies equivalent to Nondisclosure agreements (NDA) and Noncompete agreements (NCA). They’re contracts wherein the events agree to not disclose any data talked about within the settlement.
Area 2. Asset Safety Interview Questions
5. Clarify Knowledge Classification Roles.
- Knowledge Proprietor: The info proprietor is a person inside the group who has final duty for the safety and administration of particular datasets.
- Knowledge Custodian: The info custodian is answerable for implementing and imposing knowledge classification insurance policies and controls to guard labeled knowledge.
- Knowledge Steward: The info steward manages and maintains particular datasets or knowledge domains each day.
- Knowledge Topic: A knowledge topic is a dwelling particular person whose private data is being collected, saved, processed, or in any other case dealt with by a corporation or entity.
6. Clarify the Data life cycle.
The knowledge life cycle refers back to the levels by way of which data passes from its creation or acquisition to its disposal. That is generally utilized in data administration to grasp and handle the stream of knowledge inside organizations.

- Create: The knowledge life cycle begins with the creation or acquisition of information. This will embody producing new paperwork, creating databases, extracting knowledge from exterior sources, or receiving data from prospects, suppliers, or different stakeholders.
- Retailer: As soon as created, data is saved and arranged for straightforward entry and retrieval. This may occasionally contain saving recordsdata to a community drive, storing knowledge in a database, or organizing paperwork in a content material administration system.
- Use: Licensed customers entry and use the data for numerous functions. This will embody analyzing knowledge for decision-making, sharing paperwork with colleagues, or utilizing data to finish duties or initiatives.
- Share: Throughout this stage, licensed customers entry and share the data for numerous functions. Data is shared by way of communication channels equivalent to e mail, immediate messaging, video conferencing, or inside social platforms. Entry to data is managed to make sure that solely licensed people or teams can view or modify it.
- Archive: When knowledge is not actively used for day-to-day operations, data could also be transferred to long-term storage for archival functions. Archiving includes transferring data from energetic, main storage to secondary storage or archival methods designed for long-term preservation.
- Destroy: If data is not needed or required to be retained, it’s securely disposed of or destroyed to forestall unauthorized entry, misuse, or publicity. Destruction strategies might embody shredding bodily paperwork, wiping or degaussing magnetic media, or securely deleting digital recordsdata utilizing knowledge destruction software program.
7. What are some strategies to guard knowledge in transit?
Knowledge in transit refers to data that’s actively being transferred or transmitted between methods, networks, or gadgets. This will embody numerous sorts of knowledge, equivalent to emails, recordsdata, messages, or streaming media, because it travels from a supply to a vacation spot over a community.
- Finish-to-Finish Encryption: E2EE is a safety measure that protects knowledge throughout transmission by limiting entry to solely the sender and the meant recipient(s). Finish-to-end encryption secures knowledge on the sender’s gadget, retains it encrypted because it travels throughout the web, and decrypts it solely when it reaches the recipient’s gadget.
- Hyperlink Encryption: Hyperlink encryption is a technique used to safe knowledge because it travels throughout a communication hyperlink or community section. In hyperlink encryption, knowledge is encrypted and decrypted on the endpoints of the communication hyperlink, making certain that the information stays safe because it traverses the community.
- Onion Community: The Onion Community, sometimes called the Tor community, is a really efficient technique of defending knowledge in transit, because it goals to supply anonymity and privateness for customers when accessing the web. The identify of the community is in reference to the layers of encryption used to guard person knowledge.
8. What are some strategies for Data Obfuscation?
Data obfuscation strategies are methods that obscure or conceal delicate or confidential data, which is employed to guard knowledge privateness, mental property, or delicate data.
- Concealing Knowledge: It fully removes entry to delicate knowledge. Concealing includes changing delicate knowledge with placeholder characters or tokens whereas preserving the information format and construction. For instance, masking can be utilized to hide parts of bank card numbers, social safety numbers, or private identification data (PII) in databases or logs.
- Pruning Knowledge: It refers back to the means of selectively eradicating or trimming pointless or redundant knowledge from a dataset, database, or storage system. The aim of pruning knowledge is to optimize storage assets, enhance knowledge high quality, and improve system efficiency.
- Fabricating Knowledge: It includes creating and inserting false or deceptive data into datasets, paperwork, or methods to obscure or shield delicate or confidential data. This method is used to deliberately introduce noise to confuse or mislead unauthorized events making an attempt to entry or analyze the data.
- Encrypting Knowledge: Encryption is the method of changing plaintext knowledge into ciphertext utilizing cryptographic algorithms and keys. Encryption helps shield knowledge confidentiality and integrity.
Area 3. Safety Structure and Engineering Interview Questions
9. Clarify any 5 safe design ideas.
- Protection in depth: Protection in depth includes implementing a number of layers of safety controls all through a system. This method ensures that even when one layer of protection is breached, different layers stay intact to forestall the danger.
- Safe defaults: Safe defaults usually undertake a “default deny” coverage for entry management, that means that entry is denied by default except explicitly allowed. This precept ensures that solely licensed customers, providers, or processes have entry to assets, lowering the probability of information breaches.
- Zero Belief: Zero Belief works on the precept of “by no means belief, all the time confirm,” that means that belief is rarely assumed primarily based on location or community topology. This method requires steady verification of belief earlier than granting entry to assets.
- Privateness by Design: Privateness by Design (PbD) is a precept that advocates for embedding privateness issues into the design and growth of methods. PbD is intently associated to safe design ideas because it goals to make sure that privateness protections are built-in into the structure and performance of the system, alongside safety measures.
- Shared Accountability: Shared duty is a safe design precept that emphasizes the collective duty of a number of stakeholders—equivalent to builders, directors, customers, and third-party service suppliers—in making certain the safety of methods, purposes, and knowledge. This precept acknowledges that no single entity may be solely answerable for safety and {that a} collaborative effort is required to guard towards threats.
10. What are Safety fashions? Clarify anyone safety mannequin.
Safety fashions are conceptual frameworks used to implement safety insurance policies and entry controls inside a computing setting. These fashions present a structured method to managing safety necessities. There are a number of safety fashions. One such safety mannequin is the Bell-LaPadula mannequin.
The Bell-LaPadula mannequin is a safety mannequin used primarily for confidentiality enforcement in pc methods. This mannequin has turn out to be a foundational idea within the area of pc safety. The mannequin relies on the precept of obligatory entry management (MAC), the place entry to assets is set by safety labels related to topics and objects. Within the Bell-LaPadula mannequin, Every bit of knowledge and every person within the system is assigned a safety label that signifies its safety stage.
Some Properties of Bell-LaPadula mannequin embody:
- Easy Safety Property – No Learn: In line with the Easy Safety Property, a topic with a specific safety clearance shouldn’t be allowed to learn data at the next safety stage. Topics can solely entry data at a decrease safety stage.
- Star Property – No write: The Star Property states {that a} topic shouldn’t be allowed to put in writing data to a decrease safety stage.
- Sturdy Star Property: The BLP mannequin enforces the Sturdy Star property, which ensures that the system is extremely safe. The topic can’t learn and write the recordsdata on the higher Layer or the decrease Layer.
11. Clarify TCSEC and ITSEC.
TCSEC and ITSEC are two Analysis standards methods for measuring safety architectures.
Trusted Pc System Analysis Standards (TCSEC)
Trusted Pc System Analysis Standards, also referred to as The Orange Ebook, is a well known framework for evaluating pc system security measures. It was developed by the U.S. Division of Protection (DoD) within the 1980s.
The classification ranges beneath this analysis standards are:
Class A – Verified Safety
Class B – Obligatory Safety Safety
Class C – Discretionary Safety Safety
Class D – Minimal Safety
The Orange Ebook solely measures the confidentiality of single-box architectures. Due to these limitations, Data Know-how Safety Analysis Standards (ITSEC) was designed.
Data Know-how Safety Analysis Standards (ITSEC)
The Data Know-how Safety Analysis Standards is a safety analysis framework Developed within the late 1980s by a number of European international locations to supply a standardized methodology for evaluating the security measures and capabilities of pc methods. ITSEC had ‘E’ ranges of assurance. E ranges vary from E0 to E6.
12. Easy methods to scale back threat in mobile-based methods?
Cell Machine Administration (MDM) and Cell Software Administration (MAM) options assist organizations safe cell gadgets and purposes. Some methods to scale back threat in mobile-based methods are:
- Coverage Consciousness: Use insurance policies like Acceptable Use, BYOD/CYOD (Convey Your Personal Machine/Select Your Personal Machine), together with correct training, consciousness, and coaching.
- Distant Entry Safety: Distant entry safety is essential for lowering dangers related to mobile-based methods, because it ensures that licensed customers can securely entry company assets and knowledge from distant areas whereas minimizing the potential for unauthorized entry and knowledge breaches. VPN capabilities must be enabled.
- Endpoint Safety Options: MDM-provisioned software program must be put in on cell gadgets to implement safety insurance policies, monitor gadget well being, and detect and reply to safety threats on distant gadgets.
- Software Whitelisting: Whitelisting may be carried out by organizations to manage which purposes must be put in on the person’s gadget. Software whitelisting can nonetheless be a invaluable safety measure for cell gadgets, serving to to mitigate dangers related to unauthorized or malicious software program execution.
Area 4. Communication and Community Safety Interview Questions
13. What are the steps you adopted to arrange Wi-Fi in your house?
Step 1: Select a Wi-Fi Router
Choose a Wi-Fi router that meets your web utilization wants.
Step 2: Join the Router
Join the router to your web modem by way of Ethernet cable. Most routers have a WAN port the place you’ll join the modem.
Step 3: Entry Router Settings
Join a tool to the router’s default Wi-Fi community or join immediately by way of an Ethernet cable. Open an internet browser and sort the router’s IP tackle within the tackle bar. Log in to the router’s administration interface utilizing the username and password offered within the router’s documentation.
Step 4: Configure Wi-Fi Settings
You may configure the Wi-Fi community identify, safety settings, and Wi-Fi password.
Step 5: Take a look at and Troubleshoot
Take a look at your Wi-Fi community to make sure that gadgets can join and entry the web reliably.
Step 6: Safe Your Community
Allow further security measures equivalent to visitor networks, MAC tackle filtering, and firmware updates to enhance the safety of your Wi-Fi community.
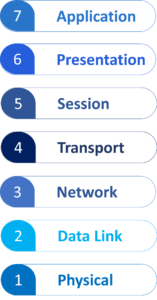
14. What’s the OSI mannequin?
OSI stands for Open Programs Interconnection. The OSI mannequin is a framework that standardizes the capabilities of a computing system into seven distinct layers. Every layer serves a selected objective and interacts with subsequent layers to facilitate communication between gadgets and methods. The seven layers are:
15. What are the Community assault phases?
Community assaults usually contain a number of phases, every designed to attain particular goals in compromising the goal community or system.
Any profitable assault could have the next phases:
- Reconnaissance
- Enumeration
- Vulnerability evaluation
- Exploitation

16. What are DoS and DDoS assaults?
In a DoS (Denial-of-Service) assault, a single attacker or a small group of attackers targets a server, community, or software by flooding it with a excessive quantity of visitors. This flood of visitors consumes the goal’s assets, inflicting it to turn out to be unresponsive.
In a DDoS (Distributed Denial-of-Service) assault, a number of gadgets, generally known as botnets, are coordinated to launch simultaneous assaults towards a single goal. These gadgets might be contaminated computer systems, smartphones, IoT gadgets, or servers managed by the attacker. The coordinated assault amplifies the affect of the assault.
Area 5. Id and Entry Administration (IAM) Interview Questions
17. What are Entry management providers?
Entry management providers seek advice from the set of mechanisms and insurance policies carried out to manage and handle entry to assets, methods, and knowledge inside a corporation’s IT setting.

- Identification is the method of uniquely figuring out people, gadgets, or entities searching for entry to methods, assets, or knowledge inside a corporation’s IT setting.
- Authentication is the method of verifying the Id of customers or entities who wish to entry a system.
- Authorization determines the assets that authenticated customers are allowed to entry primarily based on their Id, roles, permissions, and privileges.
- Accountability performs a vital function in sustaining safety, compliance, and belief by holding customers accountable for his or her actions. It’s ensuring that applicable identification, authentication, and authorization are monitored.
18. What are the three sorts of authentication?
- Authentication by data includes one thing the person is aware of, equivalent to a password, PIN, passphrase, or solutions to safety questions. These are generally utilized in username/password authentication schemes.
- Authentication by possession makes use of one thing the person owns, equivalent to a bodily token, sensible card, cell gadget, or {hardware} safety key. These tokens generate one-time passwords (OTPs) which are used for authentication.
- Authentication by attribute includes elements equivalent to biometric traits (e.g., fingerprint, iris scan, facial recognition, voice recognition, or behavioral biometrics). Biometric authentication makes use of bodily traits to confirm a person’s Id.
Two-factor authentication requires customers to make sure any of the above two elements of authentication to confirm their Id.
Multi-factor authentication makes use of two or extra authentication strategies to confirm a person’s Id.
19. What are the potential dangers associated to IDaaS?
IDaaS stands for Id as a Service. It’s a cloud-based service that gives identification and entry administration capabilities to organizations.
-
- IDaaS options retailer delicate person authentication knowledge and entry controls within the cloud, making them potential targets for cyberattacks, knowledge breaches, and safety incidents.
- Organizations that depend on IDaaS options are depending on the service supplier’s infrastructure. Any disruptions from the supplier might affect the group’s potential to authenticate customers and entry vital assets.
- Storing person authentication knowledge and identification data within the cloud raises issues about knowledge privateness.
20. How usually ought to entry evaluations be carried out?
Entry evaluations must be carried out usually to make sure that customers’ entry rights and permissions stay applicable with their roles and obligations. Entry of an worker must be reviewed and permitted by the proprietor on the change of function. Any entry that’s not wanted must be eliminated. When an worker leaves the corporate, their entry must be reviewed, and all entry must be eliminated.
Area 6. Safety Evaluation and Testing Interview Questions
21. What’s the function of safety professionals?
-
- Safety professionals assess safety dangers and vulnerabilities throughout the group’s IT infrastructure.
- They design and implement safety architectures to guard towards cyber threats.
- They use community visitors and system logs to detect and reply to safety incidents in real-time.
22. What’s the distinction between Vulnerability Evaluation and Penetration Testing?
| Vulnerability Evaluation | Penetration Testing |
| Automated | Guide |
| Carried out in minutes/hours | Carried out in a number of days |
| Non-intrusive |
Intrusive |
| Utilizing Normal scanners |
Utilizing superior methods |
23. What’s the distinction between Key Efficiency Indicators and Key Threat Indicators (KRIs)?
| Key Efficiency Indicators (KPIs) | Key Threat Indicators (KRIs) |
| Lagging Indicators | Main Indicators |
| Tracks Inside Efficiency | Tracks Inside and Exterior Dangers |
| Measured Month-to-month/Quarterly |
Measured Weekly/Every day/Hourly |
| Non-Monetary Measures |
Monetary and Non-Monetary Measures |
24. What’s Banner grabbing and OS fingerprinting?
Banner grabbing includes retrieving data from community providers or purposes by connecting to open ports heading in the right direction methods and capturing the response messages despatched by the providers upon connection.
OS fingerprinting includes analyzing community packets or responses from goal methods to establish distinctive traits or patterns that can be utilized to find out the working system.
Area 7. Safety Operations Interview Questions
25. What are the steps included within the forensic investigation course of?
Forensic investigation is a scientific course of used to gather, protect, analyze, and current digital proof associated to cybercrimes or safety incidents.
- Identification: The identification part includes recognizing the prevalence of a safety incident or potential breach.
- Preservation: Preservation is vital to forestall the destruction of digital proof.
- Assortment: Forensic investigators collect related digital proof from numerous sources, equivalent to computer systems, servers, community gadgets, storage media, logs, and databases.
- Evaluation: The evaluation part includes inspecting the collected proof to uncover insights and establish potential safety breaches.
- Reporting: Documentation is important to report findings, observations, methodologies, and conclusions reached through the investigation course of.
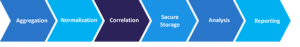
26. What are Safety Data and Occasion Administration (SIEM) methods?
Safety Data and Occasion Administration (SIEM) methods are complete options that present organizations with real-time visibility into their IT infrastructure and community safety by accumulating, analyzing, and correlating safety occasion knowledge from numerous sources.
SIEM Steps:
27. What’s Malware?
Malware refers to any kind of software program or code designed to disrupt, injury, or acquire unauthorized entry to pc methods and networks. Malware is created by cybercriminals with malicious intent and might take numerous types, together with viruses, worms, Trojans, ransomware, spyware and adware, adware, and rootkits. As soon as launched right into a system, malware might replicate itself or exploit vulnerabilities to contaminate different methods inside the identical community or group.
28. What’s Patch administration?
Patch administration is the method of figuring out, buying, testing, and making use of patches or updates to software program, working methods, firmware, and {hardware} gadgets to handle safety vulnerabilities.
Steps included in Patch administration:

Area 8. Software program Growth Safety Interview Questions
29. What’s DevOps safety?
DevOps safety, also referred to as DevSecOps, is a set of practices, methodologies, and instruments that combine safety ideas and practices into the DevOps (Growth and Operations) course of. It goals to foster collaboration between growth, operations, and safety groups to construct, deploy, and handle software program purposes and IT infrastructure securely all through the software program growth lifecycle (SDLC).
30. What’s Code obfuscation? Clarify its varieties.
Code obfuscation is a method used to hide the supply code of a software program software, making it tougher for attackers to grasp, analyze, and reverse engineer.
The three primary sorts of obfuscation are:
- Lexical Obfuscation: Lexical obfuscation is a sort of code obfuscation approach that includes altering the lexical construction of the supply code to make it tougher for people to grasp and analyze. It’s the weakest type of obfuscation.
- Knowledge Obfuscation: Knowledge obfuscation is a method used to hide delicate data with a view to shield its confidentiality and privateness. Knowledge obfuscation is often used to guard delicate knowledge in storage and transmission, significantly in situations the place encryption alone is probably not enough.
- Management Circulation Obfuscation: Management stream obfuscation is a method used to obfuscate the management stream of a software program program, making it tougher for attackers to grasp and analyze this system’s logic and conduct.
31. What’s the distinction between REST and SOAP APIs?
REST (Representational State Switch) and SOAP (Easy Object Entry Protocol) are two completely different architectural types used for designing internet providers and APIs.
Listed here are the important thing variations between REST and SOAP APIs:
| REST | SOAP |
| Representational State Switch | Easy Object Entry Protocol |
| Versatile | Inflexible |
| Primarily based on HTTP | Primarily based on XML |
| Principally Utilized in Internet Functions | Utilized in Internet Functions and Non-Internet Functions |
32. Why do Software program growth vulnerabilities happen?
Software program growth vulnerabilities happen as a consequence of quite a lot of elements, together with human error, programming errors, insecure coding practices, design flaws, inefficient testing, and lack of safety Consciousness.
FAQs
1. What kind of CISSP interview questions are requested through the CISSP Certification examination?
The CISSP certification examination focuses on assessing a candidate’s experience throughout a broad vary of cybersecurity ideas. CISSP interview questions can vary from theoretical ideas to sensible problem-solving situations. Candidates could also be requested about safety insurance policies, threat administration methods, incident response procedures, cryptography, community safety measures, and authorized or regulatory points associated to data safety. The aim is to guage the candidate’s complete understanding of knowledge safety practices and ideas with the CISSP interview questions.
2. What are the 8 domains of CISSP Certification, and what’s their significance in CISSP interview questions?
The 8 domains of the CISSP Certification are:
- Safety and Threat Administration: Focuses on insurance policies, authorized points, and threat administration.
- Asset Safety: Covers knowledge safety controls and classification.
- Safety Structure and Engineering: Offers with safe design ideas and fashions.
- Communication and Community Safety: Entails securing community structure and elements.
- Id and Entry Administration (IAM): Issues controlling entry to assets and identification administration.
- Safety Evaluation and Testing: Encompasses auditing and safety testing methods.
- Safety Operations: Focuses on incident administration, catastrophe restoration, and operational safety.
- Software program Growth Safety: Entails safety within the software program growth lifecycle.
These domains are vital in CISSP interview questions as they symbolize the core data areas that candidates are anticipated to be proficient in. Interview questions might delve into any of those domains to evaluate a candidate’s skills and understanding of knowledge safety inside these vital areas.
3. What’s the passing ratio for CISSP Certification?
The passing ratio for the CISSP Certification examination can range from yr to yr. Typically, the CISSP examination has a move price of round 20% to 30%. This low move price underscores the examination’s issue stage and the excellent understanding required throughout all eight domains. Success within the CISSP examination is indicative of a candidate’s deep data and experience within the area of knowledge safety, which is assessed by CISSP interview questions and the way the candidate solutions them.
To get the proper rating to ace all CISSP interview questions, concentrate on mastering the eight CISSP domains by way of examine and sensible software, improve your communication and problem-solving expertise, apply with mock CISSP interview questions, and keep up to date on the newest cybersecurity developments.
This brings us to the top of the ‘CISSP Interview Questions and Solutions weblog. This weblog covers the commonest CISSP Interview questions damaged down in line with the eight domains. I hope you might be clear with all of the questions and solutions. Ensure to undergo this weblog in your subsequent Cybersecurity Interview. All one of the best!
Have a question for us? Kindly tell us within the feedback part, and we’ll get in contact with you.
Edureka’s CISSP Certification Coaching Course presents the best-in-class coaching expertise that will help you get hold of the CISSP certification, together with serving to you upskill and enabling you to safe well-suited management roles within the cybersecurity trade. Incomes the CISSP Certification validates your in depth technical and managerial experience as an data safety specialist, enabling you to proficiently create, implement, and administer your group’s safety framework. Enroll at present and take your profession to better heights within the cybersecurity area!
[ad_2]
Source link



![Top 30 CISSP Interview Questions and Answers [2024 Updated]](https://decor-magazine.com/wp-content/uploads/2024/02/CISSP.png)